Note : This is the classic/original FAQ. For the very latest articles and new content for UK/Ireland users, please visit the Product Knowledgebase here
|

Wireless LAN
Security Facilities |

|
Wireless Security
If you have installed any Vigor router with Wireless LAN capability (it will have aerial sockets on the back) then the wireless facility is enabled by default. Therefore, as soon as you turn it on, and plug it in, your Internet connection is available to any PC or other device within range. That makes it very easy to use, but also means neighbours or passers by could also use your Internet connection. In some instances you might actually want that or not care, but all wireless users also have access to your PCs, as if they were plugged into the router directly. If you do not have PC Peer-to-peer networking enabled, this may provide minimal security risk, but we would still recommend that you add some security to your wireless connection.
For best security advice for your particular circumstances, we recommend you consult someone who can assess your specific risks and environment, but this general advice is provided as a good starting point :
- WEP, WPA or WPA2 Encryption - Using WEP, WPA or WPA2 encryption means that even if someone intercepts (received) your signal, the data is encrypted. Always use WPA2 where possible because WPA2/AES is a newer systems and considered to be much more secure than the WEP standard or WPA. Always use a strong (containing at least 20 non-guessable characters) password when choosing a Pre-shared key.
- SSID Name - Use a unique (For example not 'default', 'WLAN', 'wireless', 'Home', 'Joe' etc) SSID name for your wireless network because the SSID is used as salt for the Pre-Shared Key (combined with the PSK to create a unique key), so using a unique SSID makes it more difficult launch an attack using pre-compiled Rainbow Tables (a table containing the encrypted values for a huge number of PSK's to speed up password guessing)
- WPS Security - A security vulnerability (exploit) has been reported in WPS. The exploit involves part of the design of WDS, which is an industry-wide standard so whilst most DrayTek products do not use the vulnerably method, if you have a product from another manufacturer, please check with them on that product. The exploit enables a hacker to access your network, even with encryption enabled; this will enable access to your Internet connection and also computers/devices on your network. Further information regarding this is available here
- SSID Stealthing - By selecting the SSID Stealth option, it is harder to people to stumble upon your network by scanning the locality, though this does mean you cannot automatically pick up your own base station - your PC will have to be manually configured for the SSID and other local parameters. This does not make it tangibly more difficult to penetrate the WLAN but may reduce the visability of the WLAN to others
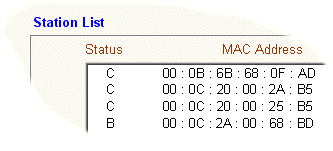
- MAC Address Locking. Each wireless PC will have a unique hardware ("MAC") address on its wireless interface (MAC is not 'Apple Mac' here). On the router you can specify the PCs which you will permit access to. A MAC address consists of 6 octets, e.g. AB F0 12 4F 12 32. If you select the router menu Wireless LAN Setup -> Station list, you can see all current visible clients. Add the PCs that you recognise and WLAN access will then be restricted. Once you add one MAC address to the router's Access Control list, all other WLAN clients must be included in the list.
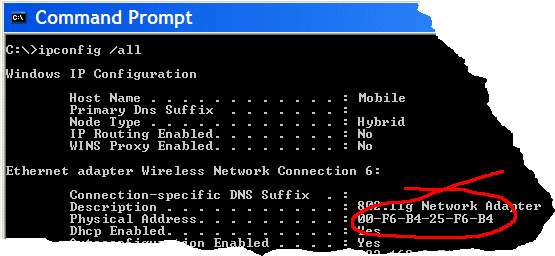
If you need to identify the client specifically (to make sure it is yours!) you can use the 'ipconfig /all' command from the Windows Command prompt on a PC to view its MAC (Physical) address:
It is possible for an attacker to by-pass mac address locking by cloning a legitimate mac address and assigning that to wireless device they are using, so in isolation this method does not provide security but it does present an additional hurdle for a potential attacker
- Isolating the WLAN - The WLAN can be isolated from the LAN by using the vlan facilities available in most DrayTek routers,
the features supported vary between devices, so check the product specification and manuals for further details.
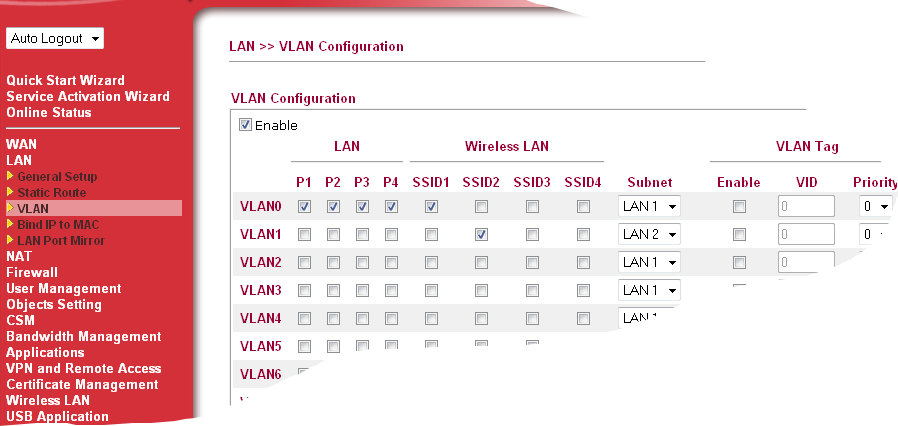
The DrayTek Vigor 2830 supports multiple subnets so SSID's could be put in a different subnet to the rest of the LAN and also separated using a VLAN.
In the screen show below, SSID1 has been put into the same subnet (LAN1) as the LAN ports and SSID2 has been put in a different subnet (LAN2). The [LAN] > [General Setup] > "Inter-LAN Routing" table then controls if the two subnets are able to communicate with each other - this is useful for scenarios where a guest WLAN is being offered.
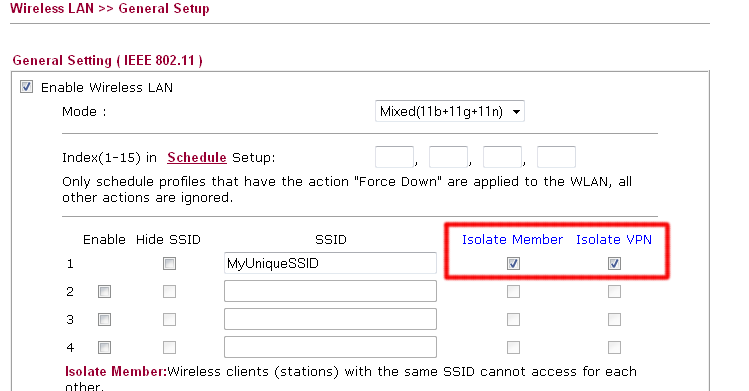
WLAN clients can be isolated from each other by ticking the "Isolate Member" check box.Ticking the "Isolate VPN" will prevent WLAN clients from communicating with VPN dial-in user or accessing LAN-to-LAN VPN's
NOTICE : This document is © SEG Communications and may not be distributed without specific written consent. Information and products subject to change at any time without notice.






